
US Cyber Command (US CyberCom) issued a malware alert on Twitter regarding the active exploitation of the CVE-2017-11774 Outlook vulnerability to attack US government agencies, allowing the attackers to execute arbitrary commands on compromised systems.
Although US CyberCom did not mention the threat actor behind the ongoing attacks, security researchers from Chronicle, FireEye, and Palo Alto Networks have linked them to the Iranian-backed APT33 cyber-espionage group.
APT33 (also known as Elfin) is an Iranian threat group with operations going as far as 2013 targeting organizations from multiple industries in United States, Saudi Arabia, and South Korea (e.g., government, research, finance, and engineering), with a focus on energy and aviation entities. [1, 2]
USCYBERCOM has discovered active malicious use of CVE-2017-11774 and recommends immediate #patching. Malware is currently delivered from: 'hxxps://customermgmt.net/page/macrocosm' #cybersecurity #infosec
— USCYBERCOM Malware Alert (@CNMF_VirusAlert) July 2, 2019
Previous APT33 warnings
US CyberCom's warning is not the only one mentioning APT33 activity since the start of 2019 seeing that the U.S. Cybersecurity and Infrastructure Security Agency (CISA) also issued a similar alert last month.
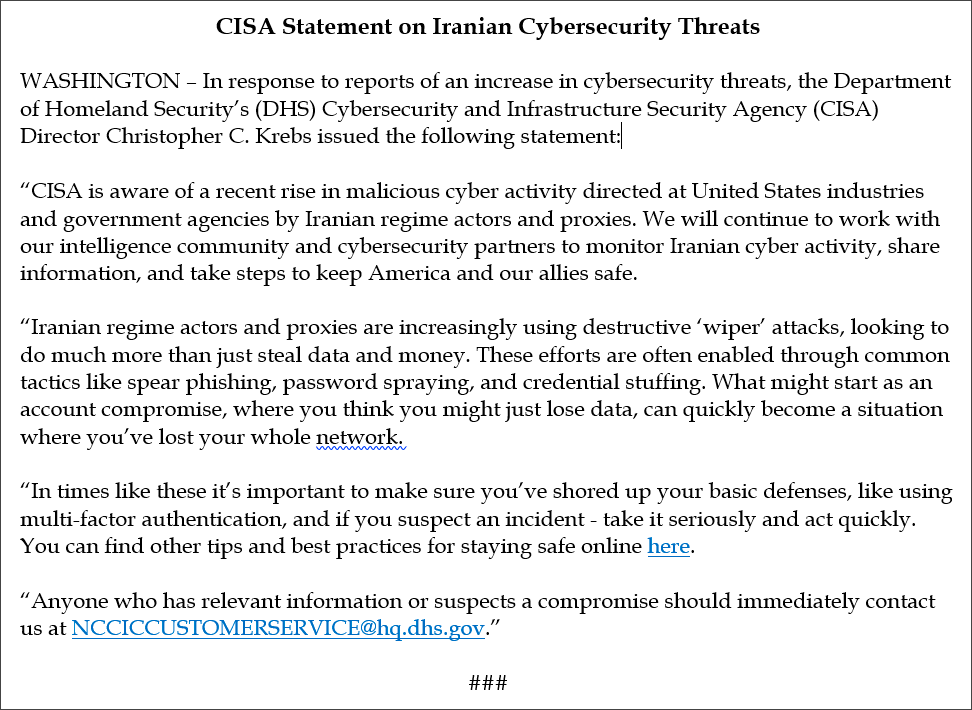
At the time, CISA Director Chris Krebs posted a statement titled "CISA Statement on Iranian Cybersecurity Threats" on his Twitter account that mentioned an increase in the number of cyber attacks which use destructive hard drive wiper tools targeting both US privately-held and government entities by Iranian actors or proxies.
Symantec, who gave APT33 the Elfin monicker, also said in March that "a recent wave of attacks during February 2019, Elfin attempted to exploit a known vulnerability (CVE-2018-20250) in WinRAR, the widely used file archiving and compression utility capable of creating self-extracting archive files."
The security outfit also hinted at the connection between APT33 and the destructive Shamoon attacks made by Chronicle, stating that "One Shamoon victim in Saudi Arabia had recently also been attacked by Elfin and had been infected with the Stonedrill malware (Trojan.Stonedrill) used by Elfin."
"Because the Elfin and the Shamoon attacks against this organization occurred so close together, there has been speculation that the two groups may be linked."
Malware used in earlier APT33 attacks
Some of the malware samples uploaded by US CyberCom to VirusTotal are malicious tools used by APT33 in previous attacks after compromising web servers as detailed by Brandon Levene, Head of Applied Intelligence at Chronicle.
"The executables uploaded by CyberCom appear to be related to Shamoon2 activity, which took place around January of 2017. These executables are both downloaders that utilize powershell to load the PUPY RAT," says Levene.
"Additionally, CyberCom uploaded three tools likely used for the manipulation and of exploited web servers. Each tool has a slightly different purpose, but there is a clear capability on the part of the attacker to interact with servers they may have compromised."
Our team spent a lot of time writing up targeted Iranian attacker #APT33's abuse of Outlook CVE-2017-11774 back in December: https://t.co/RrN3eDCA0Z
— Nick Carr (@ItsReallyNick) July 2, 2019
The malware families, Yara rules, & hunting methods shared still apply to this attacker's current campaign (mid-June to present)
FireEye's Andrew Thompson also added that the attacks US CyberCom warned about are similar to the ones described last year on FireEye Intelligence's blog, and are using RULER.HOMEPAGE payloads to drop the PowerShell-based POWERTON backdoor.
Thompson also directly attributed the ongoing Outlook attacks mentioned in US CyberCom's Twitter alert to the APT33 hacking group.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now