All About E-mail
Lawrence Abrams
- January 17, 2007
- Read 46,642 times
Table of Contents
- Introduction
- How Email Works
- E-mail Attachments
- Spam & Phishing
- Email Terms and Definitions
- Frequently Asked Questions
- Conclusion
According to a report by The Radicati Group on May 9th, 2006, there about 171 billion e-mail messages sent daily, 1.1 billion e-mail users worldwide, and 1.4 billion active e-mail accounts. These numbers are staggering and truly reflect how e-mail has become such an important medium for communicating with friends, family, colleagues, and clients. Though so many of you use e-mail all the time, how many of you truly understand how e-mail works? This tutorial is designed to give an overview of how e-mail works as well as related e-mail features. Hopefully after reading this tutorial, you will be a more informed users and consumer of e-mail products or services. This is going to be a long and detailed tutorial so I suggest you print it out and read it casually so you can absorb it all.
When we think of e-mail most of us think of a program that we run on our computer such as Outlook, Outlook Express, Thunderbird, etc where we type a message, address it, press the Send button and expect the e-mail to get to our recipient. In this section I am going to explain what happens after we press the Send button. I will use the most widely used e-mail services, SMTP and POP3 as examples, but the concepts are essentially the same for all e-mail technologies
The current Internet email standard requires all emails to be sent as ascii, more commonly known as text. When you compose a message, format it, add any attachments and press the Send button, your e-mail software will automatically convert your message into a pure text format that your mail server understands. An example of what a message with a small attachment looks like after it has been converted to text is below. As you can see there are no images or other formatting, but rather only pure text.
|
MIME-Version: 1.0 This is a multi-part message in MIME format.
------=_NextPart_000_056F_01C7396F.7EFEA840 This is an e-mail message with a small image attachment.
------=_NextPart_000_056F_01C7396F.7EFEA840
/9j/4AAQSkZJRgABAgAAZABkAAD/7AARRHVja3kAAQAEAAAAPAAA/+4ADkFkb2JlAGTAAAAAAf/b ------=_NextPart_000_056F_01C7396F.7EFEA840-- |
Once the e-mail has been converted to text, your mail software then sends the message to the outgoing mail server, or SMTP Server, you specified when you setup the mail account on your computer. When your outgoing mail server receives the e-mail, it examines the recipients, and uses DNS to determine where it needs to the send the message. It is important to remember that the mail server you send your initial message to does not know anything about the recipient. It only knows how to look up the IP address for a mail server that does know who your recipient is and send it there. Once your mail server knows what other server to send your message to, it opens a connection to that mail server and delivers the message. You can see how this is done in the figure below.
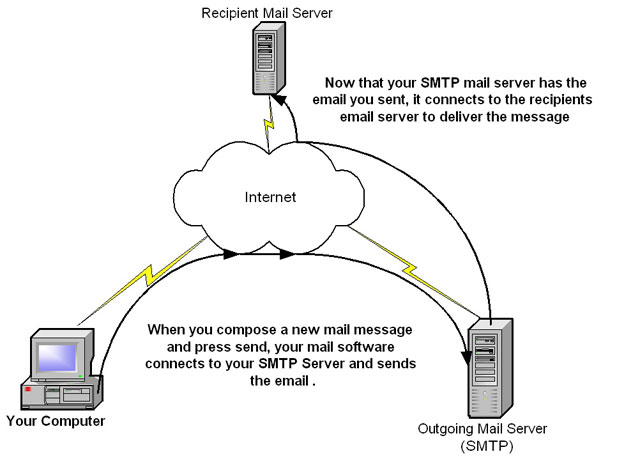
Sending an e-mail
When the recipients e-mail server receives your e-mail message, it stores the message in the recipients mailbox which is located on the server. The next time the recipient checks for their e-mail, their mail client will connect to their configured incoming mail server, otherwise known as a POP3 server. If there is mail waiting for you, your mail client will request these messages from the POP3 server and start downloading them to your computer. As each message is downloaded, your mail client will convert the message from text back to its original format. These e-mail messages will now be visible for you to read in your Inbox folder of your mail software.
It is important to note that when you download a message from the POP3 server, and do not specify to leave mail on the server in your mail account settings, then the message will be downloaded to your computer and then deleted from the POP3 server. Therefore the only copy of this message will be on your computer, so make sure you don't need it before you delete it as there is no other copy elsewhere. An example of how POP3 works can be seen in the image below.
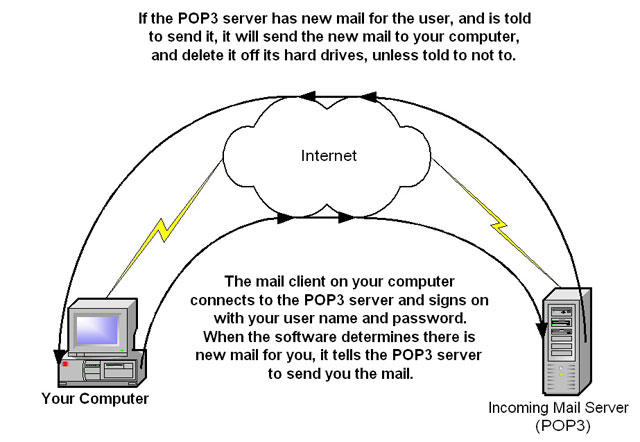
Retrieving your e-mail via POP3
I am sure most of you know what attachments are, but for those who do not we are going to give a brief course on attachments and how they work. When you send an e-mail message you have the ability to attach a file, or multiple files, of any type to your e-mail message. When you send the message these attachments are sent along with it so that when the recipient receives the message they will see your attachments and be able to open them. By far the most common use of attachments are documents, such as word or excel docs, and pictures or images.
As most attachments are not text files and as the Internet e-mail standard requires all e-mail messages to be entirely text, your mail program will process the attachments in your mail message when you send them. It does this by converting each attachment into text and sending the message like that. When the message is downloaded by the recipient's mail program, the mail program will convert these attachments back into their original form so that you can open them properly.
Let's use the image below as an example to see how it would be transformed into text by a mail software.

When the mail software sends this message, instead of the sending the message purely as binary image, it instead converts it into text and sends it that way. The image above is converted to the following text:
|
------=_NextPart_000_0621_01C73990.6DC15890 Content-Type: image/gif; name="allaboute-mail.gif" Content-Transfer-Encoding: base64 Content-Disposition: attachment; filename="allaboute-mail.gif"
R0lGODlhTgBTAJECAMe//gAAAP///wAAACH5BAEAAAIALAAAAABOAFMAQAL/hI+py+0Pj5i02ouz ------=_NextPart_000_0621_01C73990.6DC15890-- |
When the recipient downloads the mail with the attachment, the e-mail software will automatically convert the attachment back to its original form. In this way mail programs can send multiple attachments and yet still follow the Internet e-mail standards of having all messages consist of only text.
In order to open an attachment you need to have a program installed on your computer that knows how to open that file type. If you do not, your operating system will give you an error asking which program you want to use to open the file. To get around this problem, make sure you have a program installed that can open the attachment you received. To determine what program you need to install, you first need to determine the file extension of the attachment. The file extension is the last part of a filename that starts with a period and has 3-4 letters after it. For example, a file named word.doc has an extension of .doc and a file named bleeping.gif has an extension of .gif. You can then visit a site like Filext.com and do a search for the extension. This site will then tell you what program you need to install in order to open the attachment.
Remember in the introduction we said that it has been reported that there is about 171 billion e-mails sent per day? A report issued by MessageLabs.com in November 2006 states that 74% of all e-mail is spam, that one in 137.5 e-mails contain a malware of some sort, and that one in 200 e-mails is a phishing attempt. That's right ... the majority of e-mail that is sent per day is useless unwanted trash that constantly fills our inbox. For those who do not understand what this means let me define each of these terms.
- Spam
- A spam e-mail is basically unwanted and unsolicited e-mail. There are companies whose entire business model is to send out unsolicited e-mail and flood your Inbox with trash. Spammers tend to get your email addresses by either stealing or buying contact lists, when you sign up with a service that sells your information, or when someone is infected with malware and has your email address in their address book. The best way to avoid spam is to make sure you read the privacy policy of any site you enter your email address into. Also it is important to never publicly post your email address as there are programs that scan the Internet for email addresses posted publicly.
-
Malware e-mail - If an e-mail contains malware it contains a small program that if you execute it, will infect your computer with a virus, worm, Trojan, backdoor, or spyware. These programs can cause loss of data and loss of personal information such as your online banking information. It goes without saying that you definitely do not want any of these programs running on your computer. Your best way to avoid getting infected from these emails is to not open anything from someone that you do not know or trust.
-
Phishing Attempt - A phishing attempt is when you receive an e-mail that is written and formatted in such a way as to trick you into thinking they are a legitimate company. They typically masquerade as e-mails from legitimate companies such as a financial institutions and contain links back to sites that look real. The reality, though, is these sites and e-mails are all fake and are simply being used to try and steal your information so that they can attempt an Identity Theft with your information. With that said, it is advised that you never provide information such as your date of birth, social security number, or other personal information at site that you arrived at from a link in an e-mail.
To combat spam, malware, and phishing attempts it is advised that you use have installed and updated on your computer the following:
- Anti-Spyware Product such as Spybot - Search & Destroy, Lavasoft Ad-Aware, or Webroot Spysweeper
- An anti-virus product that you keep updated!
- Internet Explorer with the Phishing Filter enabled or Mozilla Firefox with its filter enabled. Instructions on how to turn these on can be found below.
I also advise that you read and follow the advice in this tutorial: Simple and easy ways to keep your computer safe and secure on the Internet
How to enable the Phishing Filter in Internet Explorer 7:
-
Open Internet Explorer
-
Click on Tools and then select Internet Options.
-
Click on the Security tab.
-
Click on the Custom Level button.
-
Scroll down to the Miscellaneous category and look for Use Phishing Filter underneath it.
-
Select Enable.
- Press the OK button. Then press the Apply and OK button again.
How to enable the Phishing Filter in Mozilla Firefox:
-
Open Firefox
-
Click on the Tools menu and select Options.
-
Click on the Security option category.
-
Put a checkmark in the checkbox labeled Tell me if the site I'm visiting is a suspected forgery
-
Select the option labeled Check by asking Google about each site I visit.
- Press the OK button.
There are many different types of software, protocols, and services available to access and send e-mail. In this section we will explain various technical terms that you may see when using e-mail services.
- POP3
- POP3 stands for Post Office Protocol version 3. POP3 software usually runs on an ISP's or company's server and accepts connections from your mail software. Once connected your mail software will send your login information, and if you successfully login, will download any new mail that may be stored on the servers to your local machine. It is important to note that a POP3 server is used only for retrieval of e-mail in a mailbox stored on the POP3 server. It is not used to actually send e-mail.
-
SMTP - SMTP stands for Simple Mail Transport Protocol. SMTP software usually runs on an ISP's or company's network, accepts mail from your mail software, and then delivers it to your recipient. It is important to note that the SMTP server is used only for sending and accepting e-mail to and from other servers or accepting e-mail to be sent from your mail client. SMTP servers are not used to download e-mail saved on the server. To do that you would use the POP3 server described above.
-
IMAP - IMAP stands for Internet Message Access Protocol. This protocol is similar to POP3 in that it is used to access mail that is located on your mail server. The difference is that IMAP allows you to view and access your e-mail without downloading the e-mail to your local computer like POP3 does. This allows you to have the same access to your mail, including folders and sent items, from any computer that has an IMAP client on it. The disadvantage to IMAP is that this protocol tends to be resource intensive for the server and your mailbox can quickly grow in size because the mail is not typically downloaded. It is for these reasons that most ISP's do not offer IMAP access to your mailboxes.
-
Webmail - Webmail is simply the ability to access the mail in your mailbox stored on a server using your web browser. The most commonly used webmail applications are Gmail, Yahoo, AOL, and Hotmail.
Q: Is it true that people can read my e-mails while they travel through Internet on the way to the person I am sending them to?
A: The technical answer is Yes. Any time a message passes through a server, that server can examine the message, copy the message, or even delete the message depending on certain criteria. The reality, though, is that the majority of ISPs and companies do not do this simply because it would become overwhelming to store copies of all the mail that passes through their server. At the same time, it is always better to be safe then sorry. So never send personally identifiable information such as social security numbers, credit card and banking information, passwords, etc via e-mail.
Q: Who or what is this Mailer-Daemon or Postmaster that sometimes sends me an e-mail.
A: These mailer-daemon or postmaster emails are automatically generated by the mail server software when an e-mail you sent failed to reach it's intended recipient for some reason. Whether it be you sent an e-mail to a person that does not exist, the recipient's mailbox is full, or the server is having an error, when you receive one of these e-mails it means that your e-mail failed to be delivered. If you open the email they will typically, if you can decode the information, give a reason as to why the delivery failed.
Q: Why does it take so long for someone to receive an e-mail I sent them?
A: When you send an e-mail to someone it should get to them within minutes if not seconds. There are many factors, though, that could cause delays in delivery. Below we explain a few of these factors:
-
When a server receives an e-mail it is placed in a first-in-first-out queue. If the queue has a lot of messages in it, and the server is not a very powerful one, it could take a while for your message to be processed. This is exacerbated further as a mail message may have to pass through multiple servers each adding their own delay.
-
You may be having trouble connecting to your outgoing mail server because the server is having a problem or your Internet connection is down. You can usually see signs of this problem when the message you sent is sitting in your Outbox folder instead of appearing in your Sent folder. A e-mail in your outbox usually indicates a problem connecting to your outgoing mail server.
-
The person receiving the e-mail is having trouble connecting to their incoming mail server in order to download the e-mail you sent them.
- The recipients address was spelled wrong or the recipients mailbox is full. When you run into this type of issue you will generally receive an error back from the Mailer-Daemon with a cryptic message stating that the address could not be found or the mailbox was out of space.
Q: I keep getting messages from someone called Mailer-Daemon saying that I am sending e-mail to people that I never sent to!?!?!
A: I see this question all of the time. You check for new e-mail on your computer and a stream of e-mails from someone called Mailer-Daemon appear saying that your e-mail message to some unknown address failed. These types of messages are typically due to your own computer or someone else's computer being infected with an e-mail worm. E-mail worms typically propagate by scanning an infected computer's address book and then disguising itself as one of the contacts in this address book. It then sends an e-mail to everyone in the list or other randomly generated recipients. When these e-mails fail to deliver for whatever reason, the errors are returned to you because the worm is sending out that e-mail disguised as yourself.
If it is not your computer that is infected there is, unfortunately, not much you can do to fix these types of problems other than try and examine the Internet header of the mail message to determine the IP address of the computer that is sending the messages. You can then hopefully track the user down using this information to let them know they are infected.
Q: When someone sends me an e-mail they get a message back saying it was undeliverable because I have no space left in my mailbox!
A: When someone sends you an e-mail your mail server will store the message in a mailbox on the server. ISPs, though, will typically set a maximum allowable size for your mailbox, and if your mailbox reaches this limit, will generate error messages stating that your mailbox is full to whoever sends you an e-mail. To fix this problem download all your mail off the mail server using a POP3 client such as Outlook Express, Outlook, Thunderbird, Eudora, etc. These types of problems typically occur when someone enables the setting in the mail software to leave messages on the server. When this setting is enabled when you download new e-mail a copy is left up on the server and is never deleted.
Q: Where does e-mail get stored on my computer?
A: When your mail client downloads new mail it stores them in mailboxes on your local computer. Depending on the software you use for mail, the mailboxes will be stored in various locations. Below is a list of the default locations for the more popular mail software packages.
|
Mail Software
|
Location on your computer
|
| Eudora | C:\Program Files\Eudora |
| Mozilla Thunderbird | C:\Documents and Settings\LoginName\Application Data\Thunderbird\Profiles\random.default\Mail\Local Folders |
| Opera | C:\Documents and Settings\LoginName\Application Data\Opera\Opera\mail |
| Outlook | C:\Documents and Settings\LoginName\Application Data\Microsoft\Outlook |
| Outlook Express | C:\Documents and Settings\LoginName\Local Settings\Application Data\Identities\{IdentityCode}\Microsoft\Outlook Express |
| Windows Mail (Vista) | C:\Users\LoginName\AppData\Local\Microsoft\Windows Mail\Local Folders |
| Windows Live Mail Desktop | C:\Documents and Settings\LoginName\Local Settings\Application Data\Microsoft\Windows Live Mail desktop\user@domain.com |
Q: So which is it...is it e-mail or email?
A: Either :)
Now that you have read this tutorial I hope that you have a learned a little bit about the blessing, or the menace, of e-mail. With e-mail being such a large part of our every day life whether it be in work and or play, having a basic knowledge of the under workings always helps. As always, if you have any questions about this tutorial or e-mail in general, please do not hesitate to ask us in our forums.