
Servers belonging to the NordVPN and TorGuard VPN companies were hacked and attackers stole and leaked the private keys associated with certificates used to secure their web servers and VPN configuration files.
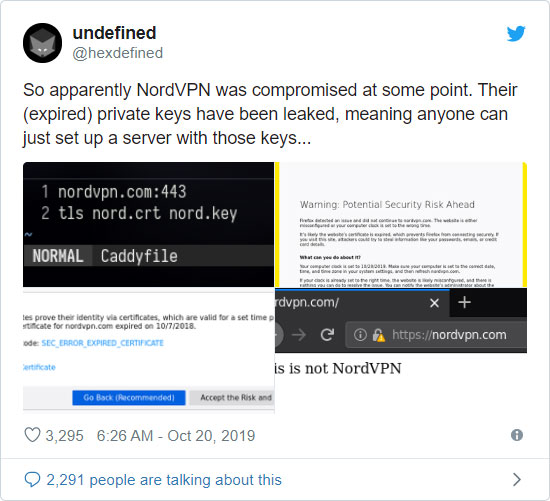
Over the weekend, security researcher @hexdefined tweeted that NordVPN, of which we are an affiliate, was compromised as the private keys for their web site certificate were publicly leaked on the Internet.
While this certificate is now expired, if this certificate was used prior to expiration it could have allowed an attacker to create a convincing site that impersonates NordVPN through the use of their certificate. More advanced attackers could have also used this key to perform man in the middle attack (MiTM) to listen in on encrypted communications.
To illustrate how a fake site could have been made using NordVPN's certificate, hexdefined shared this image.
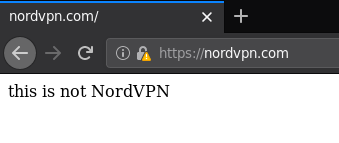
Servers for NordVPN, TorGuard, and possibly VikingVPN hacked
In addition to the web site certificate, the Twitter account for OpenVPN provider CryptoStorm.is posted a link to an 8chan post where a person hacker claimed to have full root access to servers belonging to NordVPN, TorGuard, and VikingVPN.
This allowed the attacker to steal OpenVPN keys and configuration files as shown by the image below of the NordVPN hack. CryptoStorm.is stated that by stealing these keys, it could have allowed an attacker to decrypt traffic at the time of the hack.
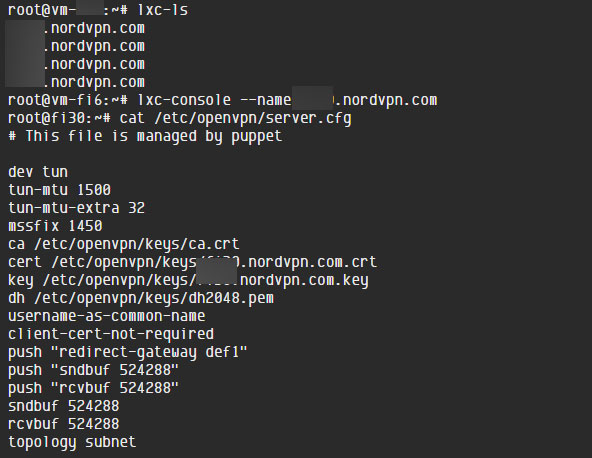
Unfortunately, NordVPN was not alone.
This same 8chan post also links to the output of hacks on a server belonging to TorGuard where a Squid proxy certificate and OpenVPN keys and configuration files were stolen.
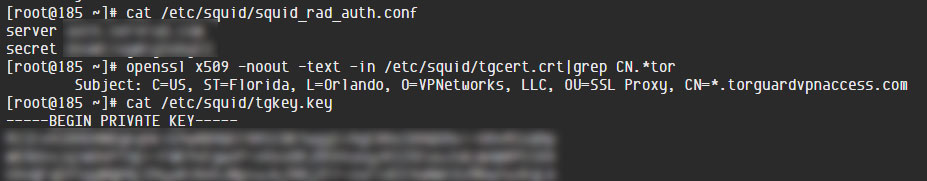
Finally, a third link goes to an alleged hack of a server owned by VikingVPN where the attacker stole OpenVPN keys and configuration files.
NordVPN and TorGuard issue statements
While VikingVPN has not responded to any of our queries, both NordVPN and TorGuard have issued statements.
According to a statement issued by NordVPN, the attacker was able to gain access to their servers through an insecure remote management tool deployed by their datacenter.
"We became aware that on March 2018, one of the datacenters in Finland we had been renting our servers from was accessed with no authorization. The attacker gained access to the server by exploiting an insecure remote management system left by the datacenter provider while we were unaware that such a system existed. The server itself did not contain any user activity logs; none of our applications send user-created credentials for authentication, so usernames and passwords couldn’t have been intercepted either. The exact configuration file found on the internet by security researchers ceased to exist on March 5, 2018. This was an isolated case, and no other datacenter providers we use have been affected."
NordVPN further states that the TLS key taken by the attacker was already expired and contrary to what Cryptostorm.io stateed, no VPN traffic could have been decrypted at the time of the attack.
In a statement by TorGuard, the VPN provider states that as they utilize "secure PKI management", none of their VPN users were affected by this breach and their CA key was not stolen as it was not present on the compromised server
"TorGuard was the only one using secure PKI management, meaning our main CA key was not on the affected VPN server."
They further state that the stolen TLS certificate for *.torguardvpnaccess.com is for a "squid proxy cert which has not been valid on the TorGuard network since 2017."
While, they do not go into details as to how the server was hacked, they do state that there was "repeated suspicious activity" at the reseller they were renting the server from and that they no longer work with them.
TorGuard further stated that the compromised server is related to a lawsuit they filed against NordVPN in 2019.
"TorGuard first became aware of this disclosure during May of 2019 and in a related development we filed a legal complaint against NordVPN in the Middle District of Florida on June 27, 2019."
More information about this lawsuit can be read at TorGuard and NordVPN.
As previously stated, VikingVPN has not responded to our queries regarding their server.
Never advertise that you can't be hacked
While using these certificates to perform a MiTM attack against TorGuard and NordVPN visitors would be difficult, one thing we have learned over time is that nothing is unhackable.
In fact, anyone who states they are unhackable or are immune to hackers are quickly proven false.
This was clearly shown, as the unveiling of this VPN hacking escapade came just hours after NordVPN decided to run a Twitter ad that stated "Ain't no hacker can steal your online life. (If you use VPN). Stay safe."
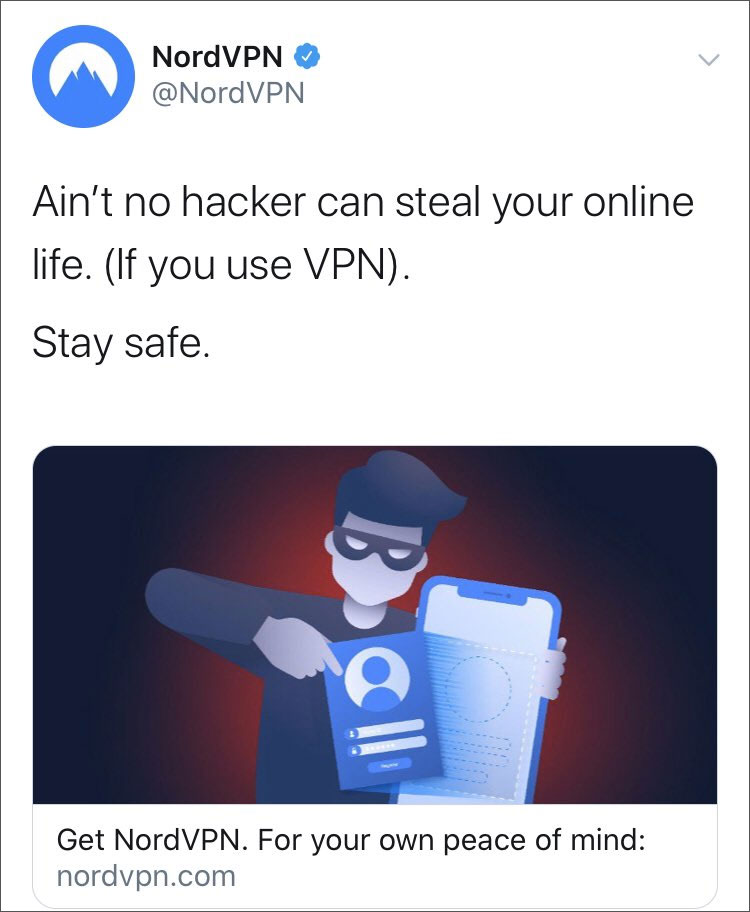
This ad was taken down soon after.
Disclosure: BleepingComputer is an affiliate of NordVPN.



Comments
CoddyHill137 - 3 years ago
No online service is 100% safe from intrusions and that includes vpns. This could have ended badly for Nord but luckily the TLS key was expired and it was only for one server and not the entire infrastructure. And Nord have already announced that they are taking extra steps to secure their systems even more so I think that they're still an ok service depending on your needs.