Demystifying the Windows Registry
Lawrence Abrams
- June 29, 2004
- Read 359,561 times
-
Table of Contents
- 1Introduction
- 2The Registry
- 3Editing the Registry
- 4Backing Up the Registry
- 5Conclusion
Introduction
Ever since Windows 95, the Windows operating system has been using a centralized hierarchical database to store system settings, hardware configurations, and user preferences. This database is called the Windows Registry or more commonly known as the Registry. When new hardware is installed in the computer, a user changes a settings such as their desktop background, or a new software is installed, this information is stored in the registry. The operating system then continually references this information during its operation. Though understanding the Registry will provide good knowledge into the inner workings of your computer, it is important to take extreme care when working with the Registry as modifying it incorrectly can cause problems with the use of your operating system.
The Registry
The registry is a key component of the Windows operating system. It is so important, that without it, Windows would not even run. When a new piece of hardware or software is installed in Windows, it stores its configuration into the Registry. This allows Windows to retrieve that information at later dates such as when it is starting up. As Windows starts it will read the configuration in the registry and know what drivers need to be loaded, what settings to be applied, and what resources need to be allocated in order for this equipment to work. Because this information is stored in the Registry on your hard drive, Windows has this information available each time it boots up.
The registry, though, is not only for operating system settings. User preferences and application settings are stored in the Registry as well. When you change your desktop background or screen saver, these details are stored in the Registry. Now when you shutdown Windows and start it up again at a later date, your preferences are available and loaded automatically. Application settings such as what directory you would like to download files to or what your default font is in a word processor are stored here as well. As you can see the Registry contains information that is not only vital to the use of the operating system, but also essential in allowing you to customize Windows to your particular tastes.
Structure of the Registry
The Registry is a hierarchical structure similar to what you see when looking at a directory/file tree on your computer. You have a main key, or Hive, with Keys, Subkeys and then Values. Each of these are discussed below:
Hives - Hives are the top most portions of the hierarchical data tree with each Hive containing a certain category of information. For example one Hive may contain the configuration that applies to the particular user logged on, while another Hive will contain information about the hardware installed in the computer. Depending on the version Windows that you are running there will be 5 or 6 different hives. Below we have outlined the 6 possible hives:
- HKEY_CURRENT_USER (HKCU) -
- This Hive contains the preferences and configuration for the particular user who is currently logged in. If a different user is logged onto the same machine, then the information in this Hive would change corresponding to that particular user's configuration.
- HKEY_LOCAL_MACHINE (HKLM) -
- This Hive contains the configuration for the actual computer. The information in this Hive remains the same regardless of the user currently logged on.
- HKEY_CLASSES_ROOT (HKCR) -
- This Hive contains the information which pertains to the core user interface such as file associations and shortcuts.
- HKEY_USERS (HKU) -
- This Hive contains the user information for all the users that have ever logged onto this computer.
- HKEY_CURRENT_CONFIG (HKCC) -
- This Hive contains the information about current hardware configuration. This Hive is linked to the HKLM Hive.
- HKEY_DYN_DATA (HKDD) -
- This Hive is found only on Windows 95/98/ME. It contains information about hardware Plug and Play. This Hive is linked to the HKLM Hive.
Keys - Keys are an organizational unit in the Registry. Keys are containers that can either contain values or further subkeys. Subkeys themselves, can contain further subkeys. Keys are similar to folders in that they can contain further subkeys or the file, or what we call values in the Registry.
Values - Values contain the actual data that is being stored in a Key or a Subkey. There are quite a few different types of values that can be stored in the Registry, but the most common that you will see are binary, strings, and DWORD values.
When visualizing the Registry you should look at the Hives, Keys, and Subkeys as the path that you will need to navigate in order to reach the final stored information which is the Value.
For example, the Registry value that controls what your initial start page will be when using Internet Explorer is HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main\Start Page, which is shown below.
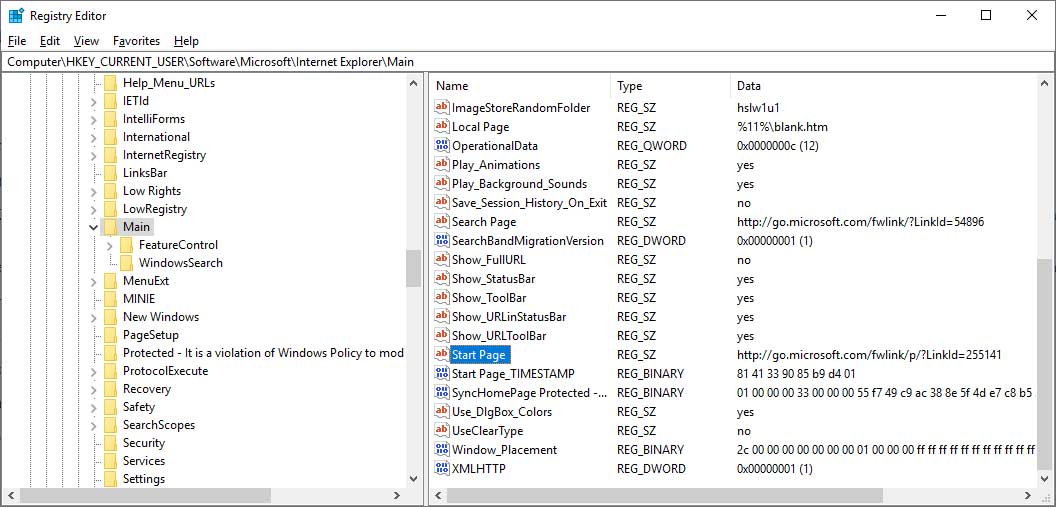
When we break this Key down to its components we can see the following:
HKEY_CURRENT_USER is the Hive that this key is associated with.
Software is a Key
Microsoft - This is a Subkey
Internet Explorer - This is a Subkey
Main - This is a Subkey
Start Page - This is the Value that the actual data is stored in. For this particular Value, the data will be the start page that you want Internet Explorer to use.
Where the Registry is stored
The Registry itself is stored on your computer in certain files. Below we detail what files and their locations are used to store the Registry based upon the particular version of Windows.
For Windows 10, Windows 8, Windows 7, Windows NT 4.0, Windows 2000, Windows XP, and Windows Server 2003, the Registry files are stored in the following directories:
%SYSTEMROOT%\System32\Config
%USERPROFILE%\ntuser.dat
The names for the registry files are:
Sam, Sam.log, Sam.sav
Security, Security.log, Security.sav
Software, Software.log, Software.sav
System, System.alt, System.log, System.sav
System, System.alt, System.log, System.sav, Ntuser.dat, Ntuser.dat.log
Default, Default.log, Default.sav
For Windows 98, the registry files are named User.dat and System.dat and are stored in the C:\Windows directory.
For Windows Millennium Edition, the registry files are named Classes.dat, User.dat, and System.dat and are stored in the C:\Windows directory.
How to edit the Registry
In order to modify values in the Registry you need to use a program called a Registry Editor. Windows comes with a program called regedit.exe or otherwise known as Registry Editor. To launch this program you should click on the Start button, then click on the Run option, and in the field type regedit.exe and press the OK button. This will launch the Registry Editor.
When you open Registry Editor you will see two panes. The left pane is your navigation pane. By default it will list all the Hives with a + or - next to each one. You can click the + to expand the tree underneath that Hive revealing Keys and Subkeys. You would keep navigating the Subkeys until you reach the desired location and then click on it once to highlight it. Then you will see in the right pane a listing of the values associated with that key.
In the screenshow below you will see an image of the Registry Editor where I have navigated to the key: HKEY_CURRENT_USER\Control Panel\Colors
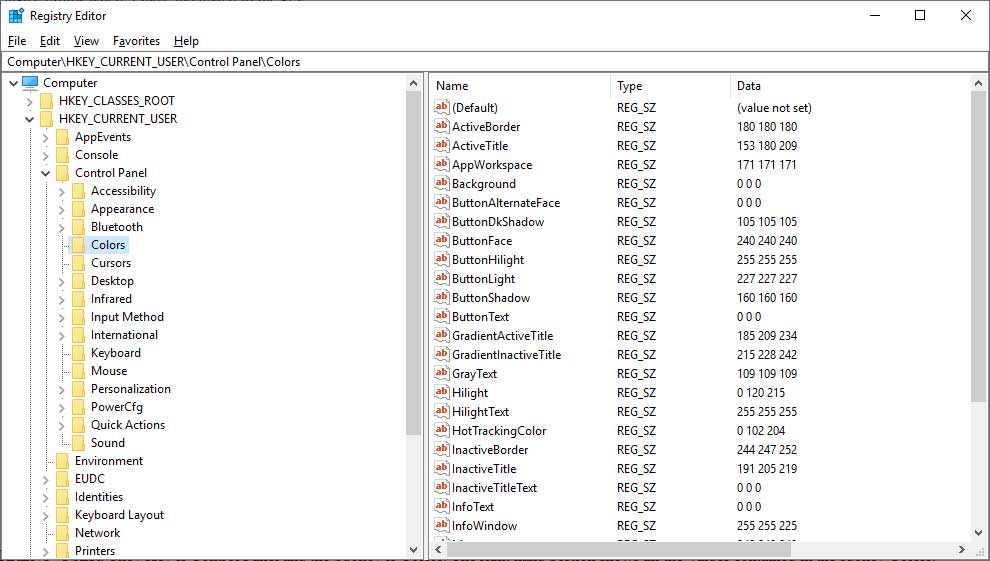
Figure 1. Registry Editor
In Figure 1 above, the Hive that we are in is HKEY_CURRENT_USER. They Key is Control Panel and the Subkey is Colors. The right hand portion shows all the Values contained in the subkey Colors.
To modify a Value, you would double-click on the value name and a screen similar to Figure 2 below would appear.
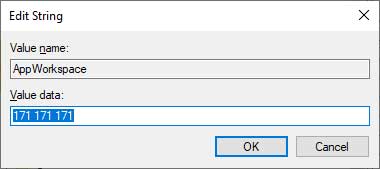
Figure 2: Modifying a Value
You then would type in the appropriate information into the Value data field and press the OK button.
To delete values, instead of double-clicking on a value name you would right-click on the value and then select Delete. This method can also be used to delete keys or subkeys. To add a value you click on the Edit menu option and then select New and pick the appropriate type.
It is also possible to export and import Registry values into your Registry. To export a particular Key or Subkey you would click once on the key you would like to export and then click on File and then Export. Then select a directory and filename to export the Registry key to. Likewise, you can also Import keys into the Registry by clicking on Import and then selecting the file that you had exported previously.
Backing up the Registry
Viruses, Spyware, and other Malware can cause corruption and damage to the Registry. With this in mind, it is important to backup your registry so that you know you have a clean copy stored safely on your hard drive in case of an emergency. Below we have outlined the steps to backup and restore your Registry under the various versions of Windows.
Please see this guide on how to Backup and Restore the Windows Registry.
Conclusion
Understanding and knowing how to backup the Registry is an important part of keeping your computer secure and running efficiently. It must be stressed that modifying any portion of the Registry should be done with the utmost care as incorrect usage of the Registry could make your computer inoperable.
As always if you have any comments, questions or suggestions about this tutorial please do not hesitate to tell us in the computer help forums.








