At this point we do not have any samples in order to analyze the infection and provide advice. If you are infected with this ransomware, please submit any samples using the following url: http://www.bleepingcomputer.com/submit-malware.php?channel=163
The contents of the HowDecrypt.txt file is similar to:
All files including videos, photos and documents on your computer are encrypted.
File Decryption costs ~ $ 500.
In order to decrypt the files, you need to perform the following steps:
1. You should download and install this browser http://www.torproject.org/projects/torbrowser.html.en
2. After installation, run the browser and enter the address: 4sfxctgp53imlvzk.onion
3. Follow the instructions on the web-site. We remind you that the sooner you do, the more chances are left to recover the files.
Guaranteed recovery is provided within 10 days.
IMPORTANT INFORMATION:
Your Personal CODE: 00000001-xxxxxx
When you visit the decryption page on TOR, you will be presented with a site that allows you to pay the ransom using .5 Bitcoins or by submitting a $500 USD MoneyPak, PaySafeCard, or Ukash voucher.
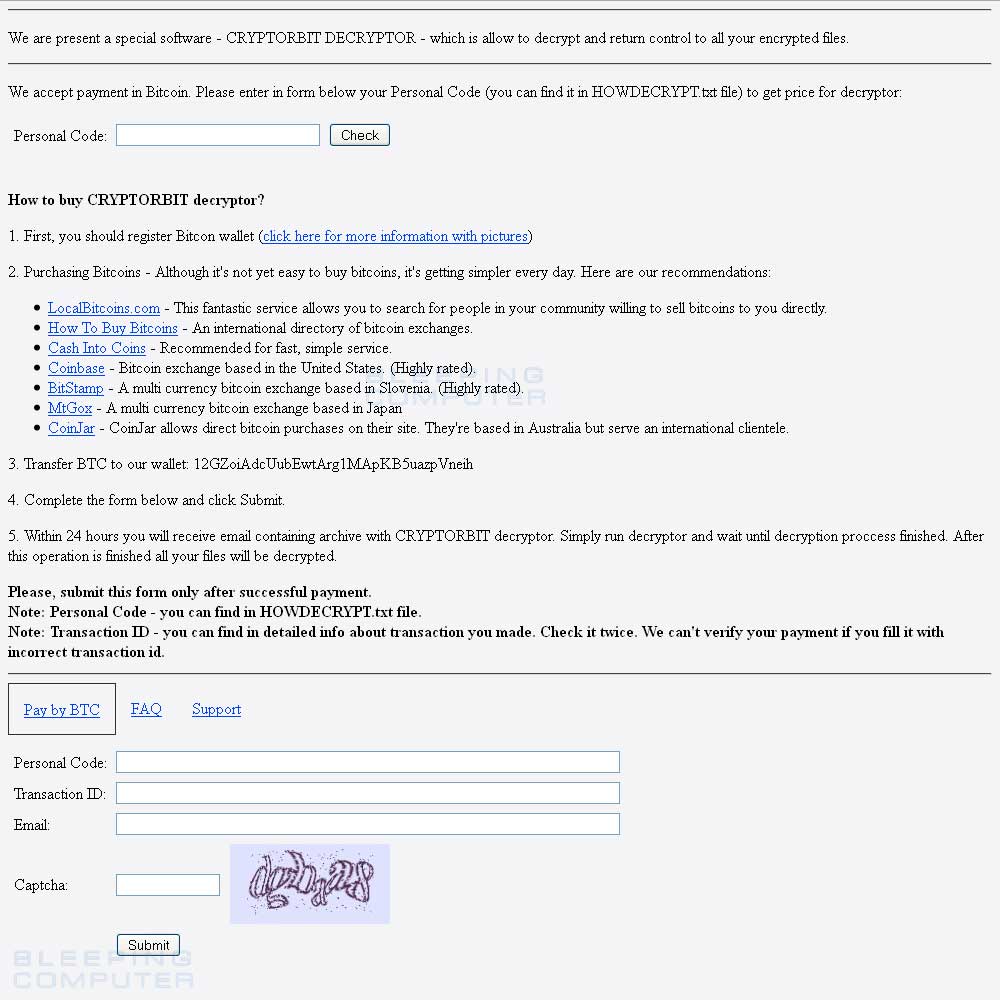
The contents of the TOR payment site is:
We are present a special software - CRYPTORBIT DECRYPTOR - which is allow to decrypt and return control to all your encrypted files.
We accept payment in Bitcoin. Please enter in form below your Personal Code (you can find it in HOWDECRYPT.txt file) to get price for decryptor:
Personal Code:
How to buy CRYPTORBIT decryptor?
1. First, you should register Bitcon wallet (click here for more information with pictures)
2. Purchasing Bitcoins - Although it's not yet easy to buy bitcoins, it's getting simpler every day. Here are our recommendations:
LocalBitcoins.com - This fantastic service allows you to search for people in your community willing to sell bitcoins to you directly.
How To Buy Bitcoins - An international directory of bitcoin exchanges.
Cash Into Coins - Recommended for fast, simple service.
Coinbase - Bitcoin exchange based in the United States. (Highly rated).
BitStamp - A multi currency bitcoin exchange based in Slovenia. (Highly rated).
MtGox - A multi currency bitcoin exchange based in Japan
CoinJar - CoinJar allows direct bitcoin purchases on their site. They're based in Australia but serve an international clientele.
3. Transfer BTC to our wallet: 12GZoiAdcUubEwtArg1MApKB5uazpVneih
4. Complete the form below and click Submit.
5. Within 24 hours you will receive email containing archive with CRYPTORBIT decryptor. Simply run decryptor and wait until decryption proccess finished. After this operation is finished all your files will be decrypted.
Please, submit this form only after successful payment.
Note: Personal Code - you can find in HOWDECRYPT.txt file.
Note: Transaction ID - you can find in detailed info about transaction you made. Check it twice. We can't verify your payment if you fill it with incorrect transaction id.
Reports state that once you submit the money, you will receive an email with an attached decrypter that you can use to decrypt your files.
Edited by Grinler, 11 February 2014 - 03:52 PM.
Added Cryptorbit info




 Back to top
Back to top











