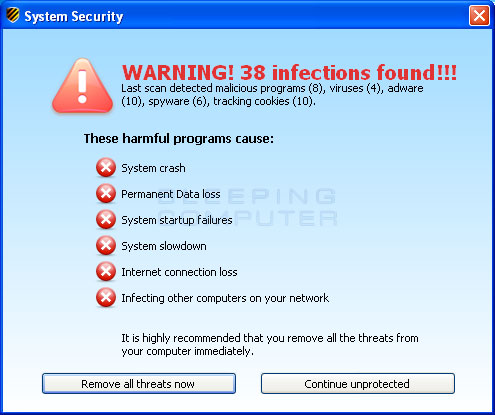
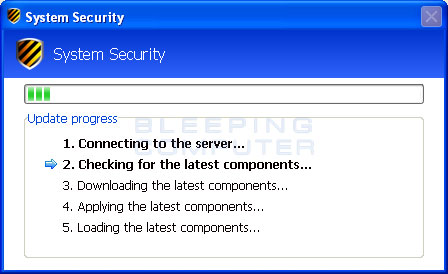
System Security is a rogue anti-spyware program from the same family as Winweb Security. This program is classified as a rogue because it uses false scan results as a method of scaring you into purchasing the software. If System Security is installed, it will be set to start automatically when you login to your computer. Once running, the program will begin to scan your computer and list a variety of infections that cannot be removed unless you first purchase the program. A dangerous problem is that System Security will list legitimate and necessary programs as infections. For example, one of the files that it states is an infection is C:\Windows\System32\svchost.exe. This file is not only legitimate, but a very important file for the operation of your computer. Without that file, your computer would not operate correctly and Windows itself may not start.
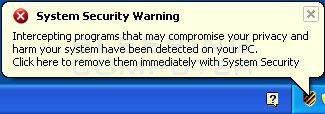
Another byproduct of System Security is that when it is running you will see a variety of false security alerts. These alerts range from warnings that your computer is being attacked to being infected with a variety of fake infections such as Lsas.Blaster.Keyloger and Spyware.IEMonster. If you click on these alerts, the program will open up a web browser and go to a page asking you to purchase the software. Just like the false scan results, these alerts are only trying to scare you into buying the program. Please ignore these alerts and instead use the free removal guide below.
This guide will walk you through removing the System Security program and its associated malware for free.
System Security Removal Options
Self Help Guide
If you are uncomfortable making changes to your computer or following these steps, do not worry! Instead you can get free one-on-one help by asking in the forums.
- Print out these instructions as we may need to close every window that is
open later in the fix.
- Before we can do anything we must first end the System Security process
as it disables the ability to run various programs, including MalwareBytes'
Anti-Malware. To do this we must first download and install a Microsoft program
called Process Explorer. Normally, we would have you use the Windows Task
Manager to terminate the process, but this rogue will disable this utility
as well. Please download Process Explorer from the following link and save
it to your desktop.
Process Explorer Download Link - Once the program has finished downloading, look for the procexp.exe file
that should now be located on your desktop. Once you find it, right-click
on it and select Rename. After you click on the Rename option,
you will now be able to change the name of the icon. Please change the name
to explorer.exe. Once the file has been renamed, double-click
on it and you will be asked to agree to the license agreement. You may also
see a screen with Windows asking if you are sure you want to run the program.
Please do so and you should be presented with a screen similar to the one
below.

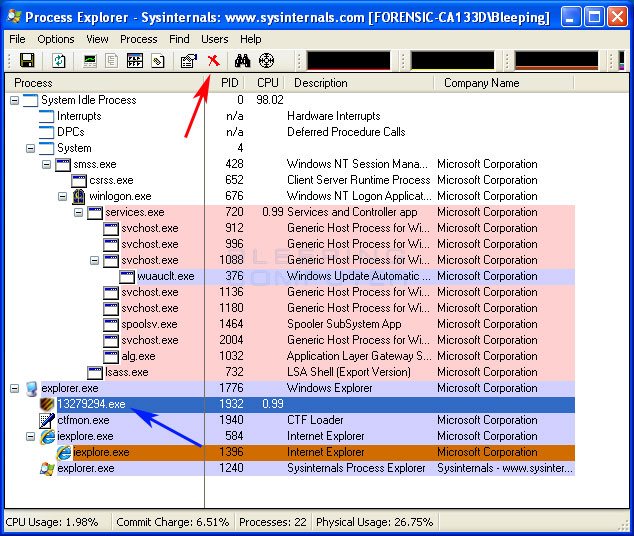
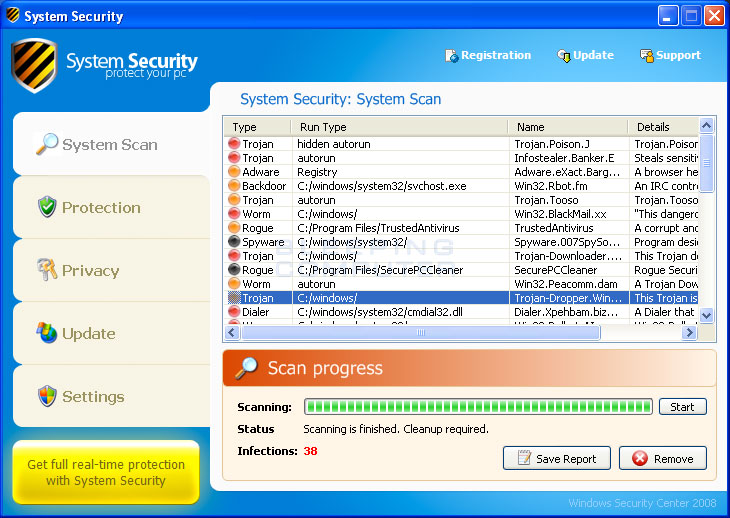
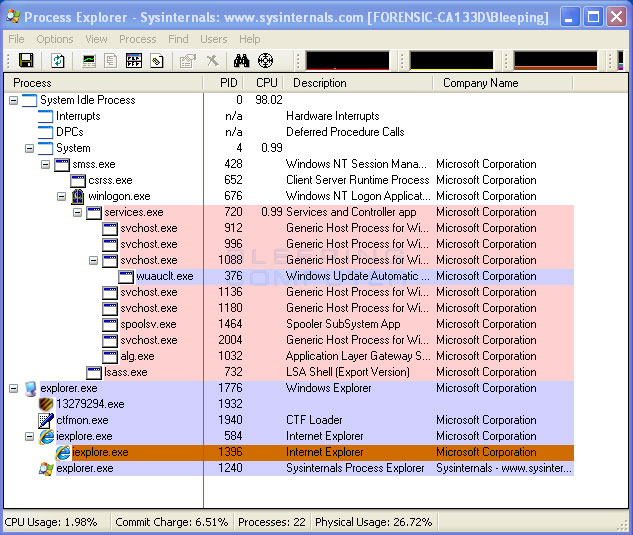
- Scroll through the list of running programs until you see a process that
has a name consisting of random numbers, such as 13279294.exe or 51231676.exe.
This process is the main System Security process, which is blocking access
to our programs. A further way to identify the process is that there will
be a small picture of a shield
 next to the process in question. When you have identified this process, select
it by left-clicking on it once so it becomes highlighted. Then click on the
red X button as shown in the image below.
next to the process in question. When you have identified this process, select
it by left-clicking on it once so it becomes highlighted. Then click on the
red X button as shown in the image below.
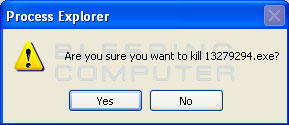
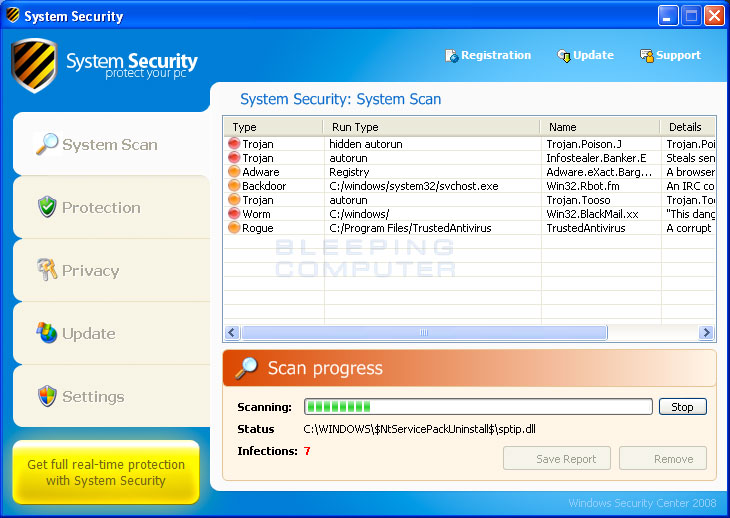
- When you click on the red X to kill the process, Process
Explorer will ask you to confirm if you are sure you want to terminate it
as shown in the image below.

At this point you should press the Yes button in order to kill the process. - At this point you should download Malwarebytes Anti-Malware, or MBAM, to scan your computer for any any infections or adware that may be present. Please download Malwarebytes from the following
location and save it to your desktop:
Malwarebytes Anti-Malware Download Link (Download page will open in a new window) - Once downloaded, close all programs and Windows on your computer, including
this one.
- Double-click on the icon on your desktop named mb3-setup-1878.1878-3.0.6.1469.exe.
This will start the installation of MBAM onto your computer.
- When the installation begins, keep following the prompts in order to continue
with the installation process. Do not make any changes to default settings
and when the program has finished installing, make sure you leave Launch
Malwarebytes Anti-Malware checked. Then click on the Finish button. If MalwareBytes prompts you to reboot, please do not do so.
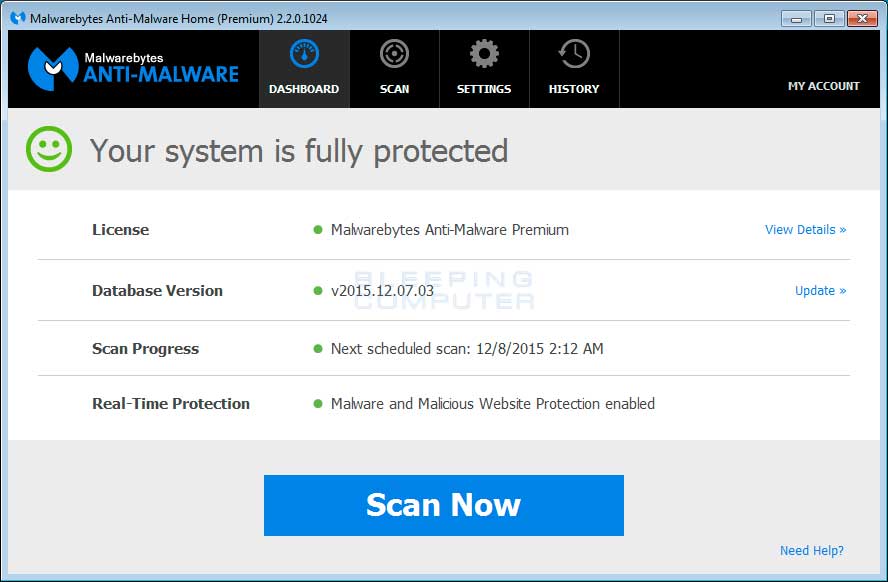
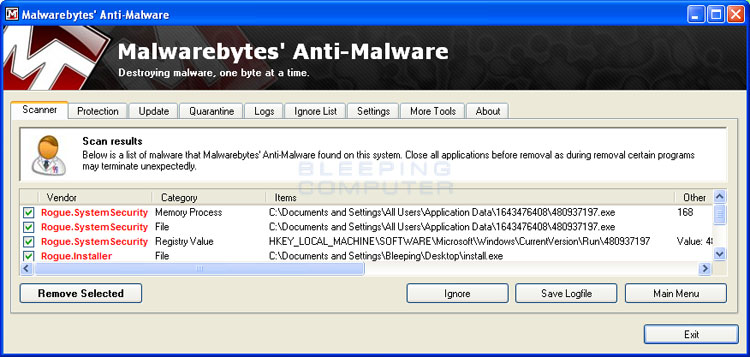
- MBAM will now start and you will be at the main screen as shown below.

Please click on the Scan Now button to start the scan. If there is an update available for Malwarebytes it will automatically download and install it before performing the scan. - MBAM will now start scanning your computer for malware. This process can
take quite a while, so we suggest you do something else and periodically
check on the status of the scan to see when it is finished.

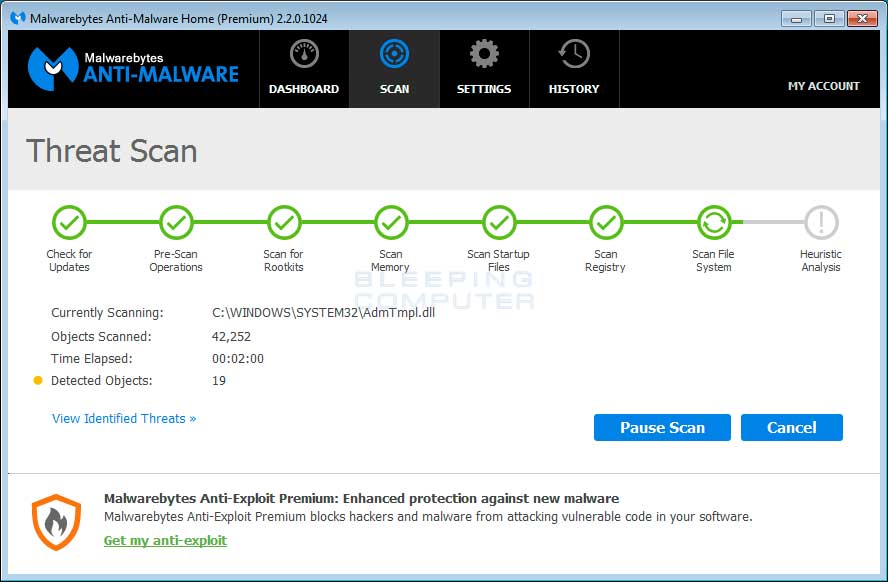
- When MBAM is finished scanning it will display a screen that displays any malware that it has detected. Please note that the infections found may be different
than what is shown in the image below due to the guide being updated for newer versions of MBAM.

You should now click on the Remove Selected button to remove all the seleted malware. MBAM will now delete all of the files and registry keys and add them to the programs quarantine. When removing the files, MBAM may require a reboot in order to remove some of them. If it displays a message stating that it needs to reboot, please allow it to do so. Once your computer has rebooted, and you are logged in, please continue with the rest of the steps. - You can now exit the MBAM program.
Your computer should now be free of the SystemSecurity program. If your current anti-virus solution let this infection through, you may want to consider purchasing the PRO version of Malwarebytes Anti-Malware to protect against these types of threats in the future.
 next to the process in question. When you have identified this process, select
it by left-clicking on it once so it becomes highlighted. Then click on the
red X button as shown in the image below.
next to the process in question. When you have identified this process, select
it by left-clicking on it once so it becomes highlighted. Then click on the
red X button as shown in the image below.